Configure Okta OpenId Connect (OIDC)
OpenID Connect (OIDC) is an authentication protocol that sits on top of the OAuth 2.0 framework, strengthening the predictability and security of connections with third-party applications. You can configure Okta OIDC as your preferred authentication method in your Tonkean board, enabling Okta SSO as the sole sign-in method for your organization.
Tonkean currently supports service provider-initiated authentication (SSO) flow only.
Prerequisites
You must have a Tonkean enterprise license and be authorized as an enterprise owner.
You must have the Tonkean Okta OIDC application configured.
Set Okta as the Preferred Authentication
In Tonkean, select your profile icon in the upper right.
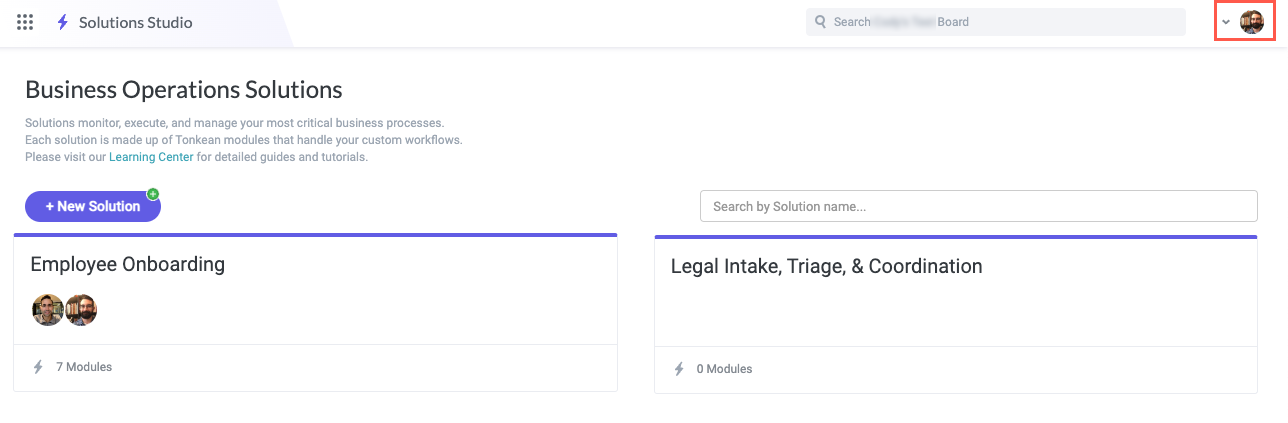
Select the <Enterprise Name> Administration in the dropdown. The Enterprise Administration screen displays.
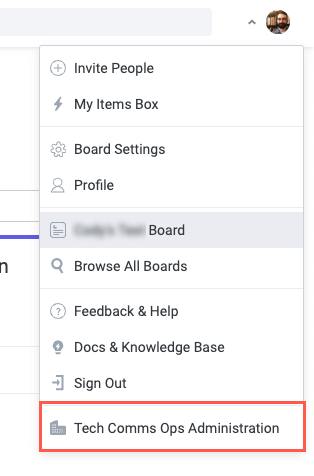
Locate the Preferred authentication method section and select No restrictions.
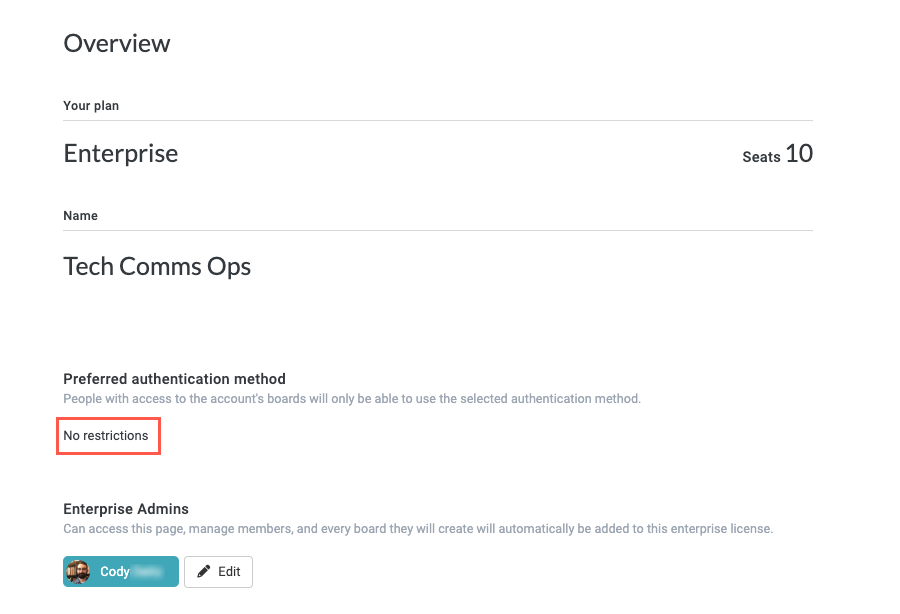
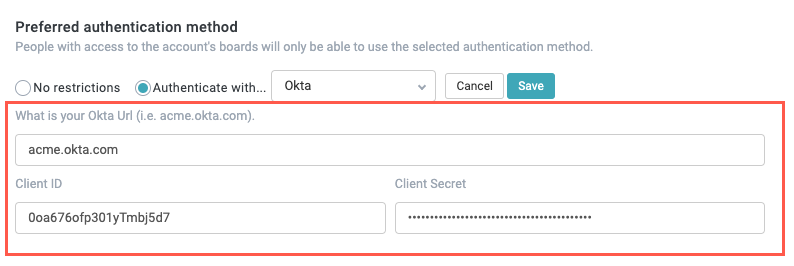
Select Authenticate with, then select Okta from the dropdown. Okta authentication fields display.
Enter the Okta environment URL for your organization, as well as the Client ID and Client Secret, all retrieved from your Okta application.
Enter the email domains for your organization to route them directly to the authentication URL.
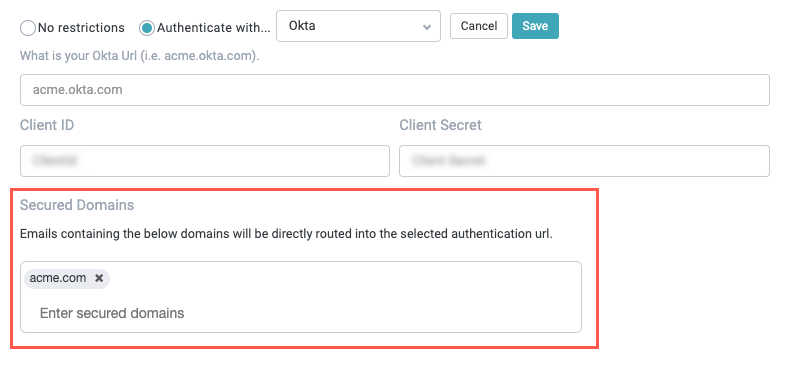
When finished, select Save. The Okta authentication fields close.
Sign in Using Okta SSO
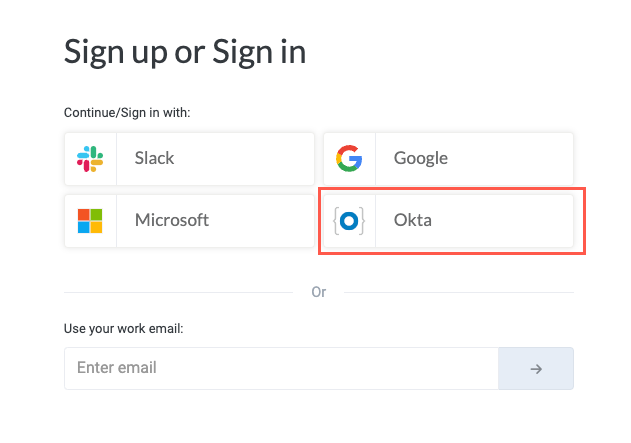
After setting Okta as the preferred authentication method for your organization, all users at your organization must select the Okta SSO option on the Tonkean Sign In screen:
Select Okta. The Login with Okta screen displays.
Enter the work email and select Login. Your email is validated and you are logged into Tonkean using Okta OIDC.
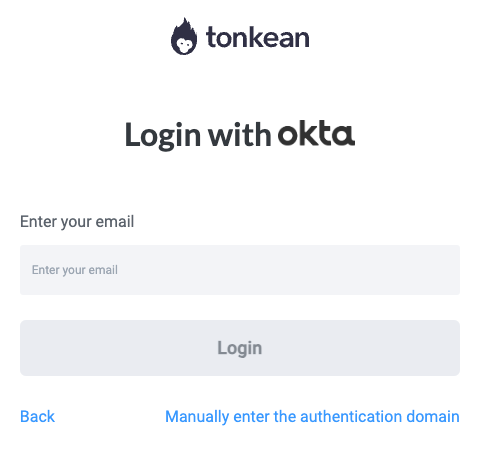
Alternatively, you can select Manually enter the authentication domain to log in:
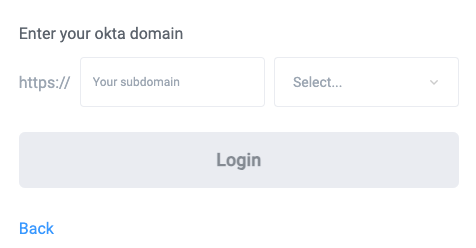
Enter your Okta login credentials and sign in to Tonkean